Introducing Private Repo Scanning for MCP Servers to Help Build Secure-by-Default MCP Servers
Feb 9, 2026
As MCP servers rapidly become core execution infrastructure for AI agents, security gaps are emerging faster than teams can spot them. Private Repo Scanning gives builders early, actionable visibility into MCP risks—before agents act in production—without slowing development.
Harold Byun, CPO at BlueRock
Why This Matters Now and the Problem
Model Context Protocol (MCP) servers have quickly evolved in the past year to become the standard for how agents execute tools. Organizations are moving en masse to adopt MCP and replace exposed services to accelerate agentic development and drive towards outcome oriented tools vs. singular function calls mapped to an API.
With any emerging standard, there can be challenges in the definition of best practices and the discovery of security imperfections or vulnerabilities. When combined with rapid-scale adoption and deployment, steps can be missed that can leave organizations exposed to unintended actions or security gaps in their MCP deployment.
For example, last month we published our own research on how an unbounded URI call could be used to take over a cloud infrastructure account by fetching credentials from a cloud instance metadata service. We found this security gap in a MIcrosoft Markitdown MCP server with over 86,000 stars and our analysis from our MCP Trust Registry (mcp-trust.com) of over 8,000 MCP servers indicates that 36.7% of published MCP servers have the same vulnerability.
This suggests that a significant gap in best practice knowledge on how to build, secure and deploy MCP servers continues to exist.
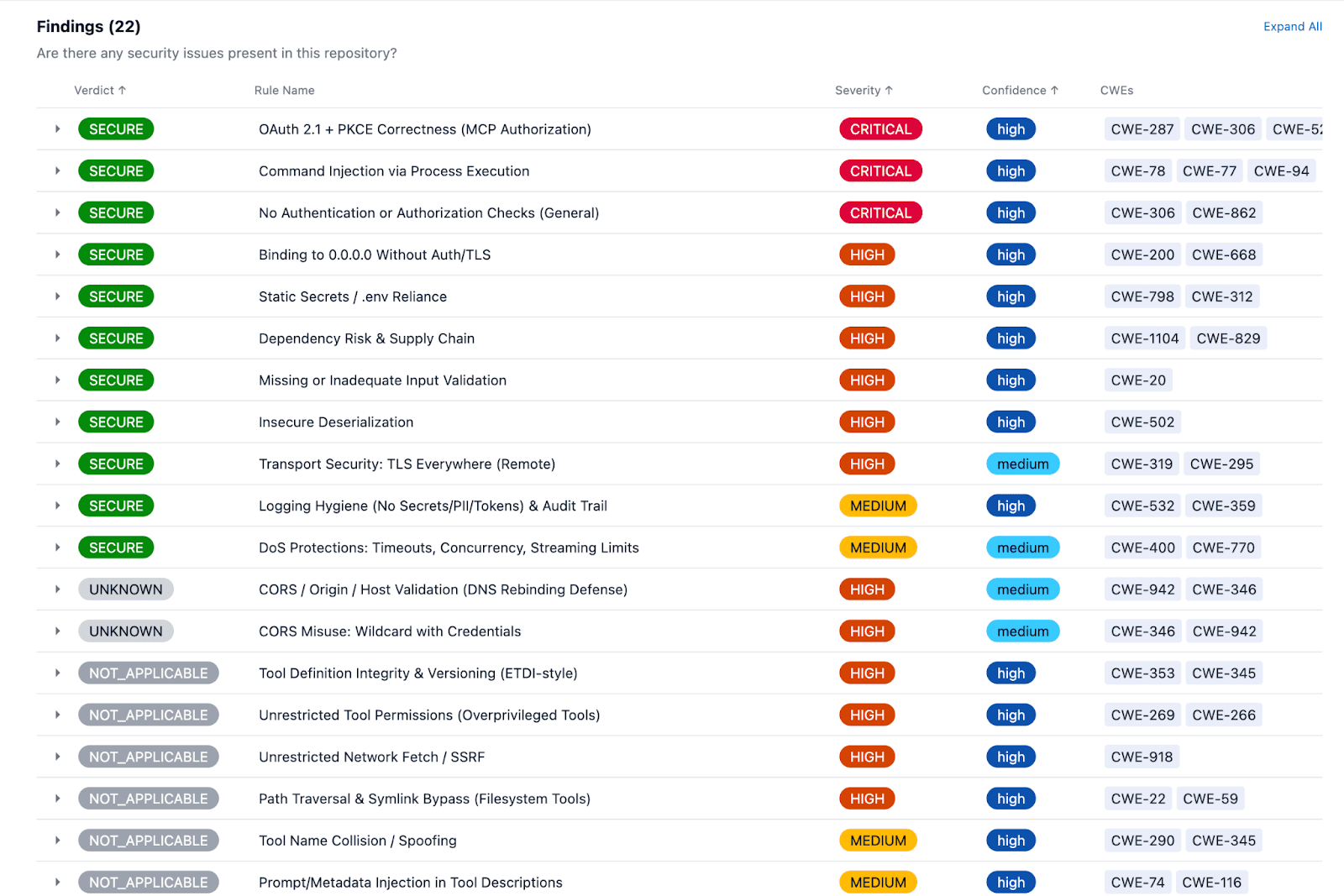
Sample of a Low Risk MCP Server Findings:
Introducing Private Repo Scanning for MCP Servers
Despite the growth in public MCP repos, current adoption of MCP remains largely concentrated internally in an enterprise organization. Since launching the registry in December, we’ve had numerous customer requests for private repo scanning, so that organizations can assess their internal MCP deployments as they look to operationalize agentic workflows.
As mentioned above, the MCP Trust Registry was established as a community resource to provide MCP builders and developers with visibility into MCP server builds and potential security vulnerabilities in those builds.
The registry initially targeted public GitHub repos and performs a security analysis across twenty-two rules mapped to governance frameworks such as OWASP MCP Top 10, MAESTRO and others. The analysis performs code level analysis and provides evidence of the code down to the line level mapped to the MITRE Common Weakness Enumeration (CWE) framework. Security rules can be viewed in the registry itself, but below is a partial summary of the types of fundings:
Unrestricted Network Fetch and SSRF
Command Injection via Process Execution
Denial of Wallet / Cost Controls
Dependency Risk & Supply Chain
Transport Layer Security
With this release update, we are now supporting private repository scanning for customers so they can easily submit their MCP servers for an analysis and review any security findings along with remediation guidance.
How Does This Help Builders?
Because MCP servers are so simple to build and deploy, it is easy to overestimate their functional state with production readiness. Scanning server builds provides developers with a set of findings grounded in security best practices with remediation guidance to easily fix any discovered security gaps.
These are standard operational gates in any software release process, the difference lies in the fact that MCP servers become part of the agentic execution fabric and open access to a b try broad range of access calls and data sources.
Applying the same rigor to MCP servers can give developers and agentic teams the confidence that privilege escalation gaps via an MCP execution layer are not exposed.
Early Indicators of Success
Raising awareness amongst developers of MCP servers has shown demonstrable improvement. Dozens of builders have submitted their builds for scans and have quickly implemented remediation guidance.
Adspirer, an ad tech firm, integrating MCP into their core offering have utilized the private repo scanning to assess their AI and MCP implementation and used the findings to convey a stronger security posture and rigor to their customers.
Other early adopters have implemented fixes and submitted rescans in the same day. This is a strong indicator that agentic builders want to do things the right way. They simply need the tools and guidance to help them make the better decisions.
A customer recently told us, “we want the easy way to be the right way”. MCP certainly makes things easy — however, it is incumbent on agentic teams to ensure the build and deploy is “the right way”.
Where Do We Go From Here?
With over 600 vulnerabilities discovered in the latest Anthropic Opus 4.6 release, a path to security uncertainty has been exposed. The future of vulnerability exposures only increases exponentially from here and the need for builders and AI teams to adopt secure-by-default approaches becomes even more critical.
The maturation of MCP and its increasing adoption is dependent on developers adopting best practices and organizations integrating a business-first strategy that incorporates security as part of their agentic success.
Check your MCP servers:
Browse 8,000+ public servers and submit your private MCP Server for scan: mcp-trust.com
