The Technical Limits of MCP Gateways for Agentic AI
Feb 10, 2026
MCP gateways can address some security and visibility concerns in agentic AI workflows, but they also introduce non-trivial technical and operational challenges. Latency, scale, certificate management, availability, and new attack surfaces all become part of the system once a gateway is placed in the execution path. In this post, we examine the limitations of MCP gateways from an engineering and operations standpoint, based on how these systems behave at scale in real deployments.
Efi Gatmor, VP of Engineering at BlueRock
Introduction
The rapid adoption of Model Context Protocol (MCP) Servers and their use in Agentic AI workflows poses new security, visibility and control challenges for the Enterprises. Similar to the introduction of the Network Firewall in the past, many organizations are considering solutions based on MCP Gateways as a possible way to tackle these challenges. This approach might mitigate some of the security, visibility and control concerns but it also introduces several new non-trivial challenges for the organization.
In this short blog, I will point out some of those technical challenges and the impact they may have on the organization’s agentic AI projects.
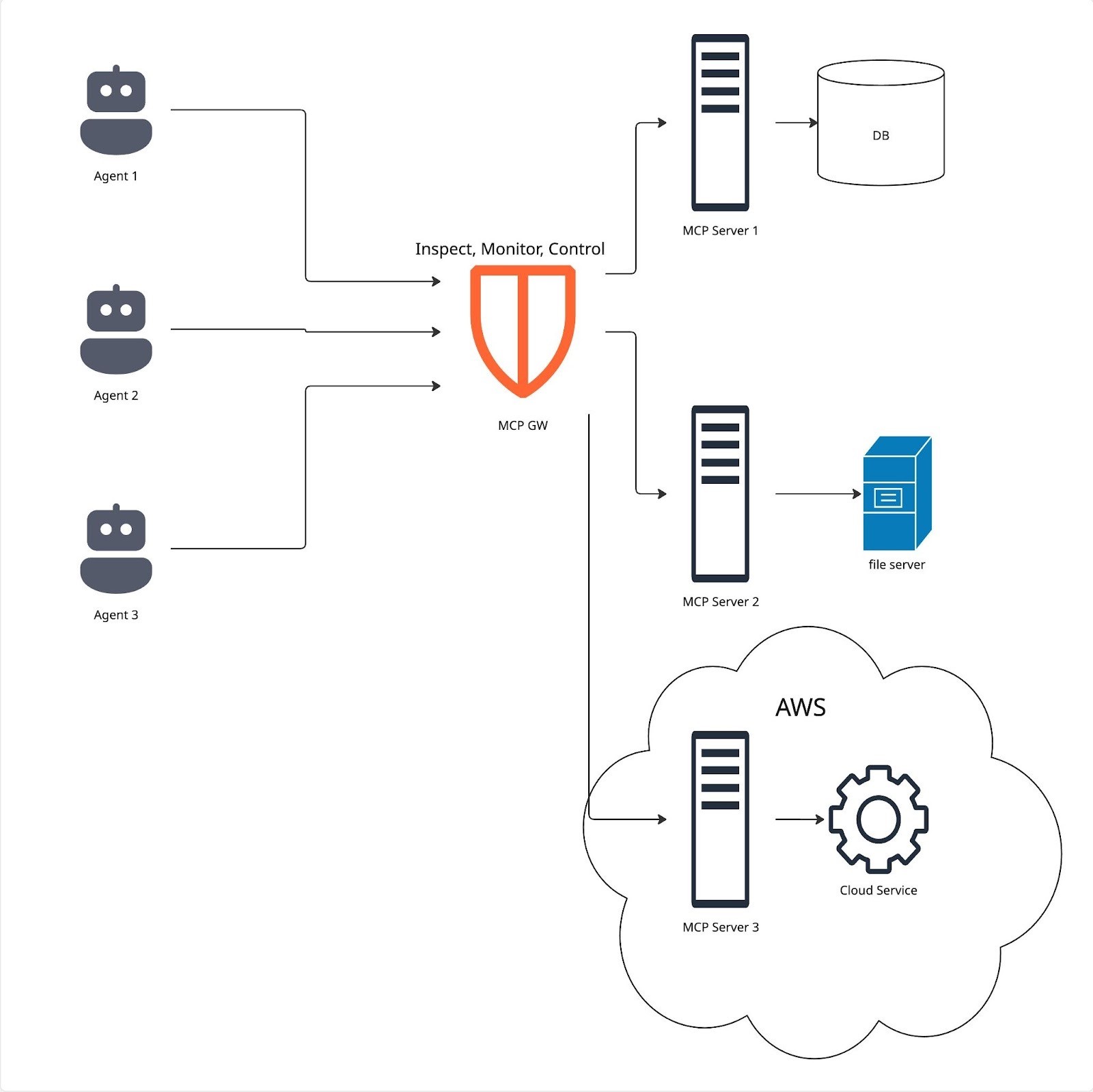
Performance, Scalability and Reliability
The MCP gateway functions as a network man-in-the-middle proxy that intercepts the AI agents’ connect requests, decrypts the traffic, inspects it, encrypts it again and sends it to the MCP server. It then gets the reply from the MCP server, decrypts the traffic again, inspects it, encrypts it and sends it back to the agent. It might log and display that information as well.
Added Latency
The MCP gateway adds a non-negligible amount of latency to traffic that could impact the agent performance. The impact for low latency, high speed transactions could hurt productivity and could become a major bottleneck. It may also tempt the developers and Operations to bypass the MCP gateway all together.
Scalability Requirements
The MCP gateway performance is dependent on the number of Agents, MCP Servers, Tools and the size of data. Large deployments will increase the amount of CPU, memory and storage requirements and could slow down the performance of the gateway. In order to scale, the organization might need to invest in complex load-balancing and cluster architectures. As the deployment grows, the MCP gateway could become a bottleneck that will hurt performance.
Reliability
The MCP Gateway is a single chokepoint and single point of failure. If it fails, the entire agentic workflow breaks. The organization might need to invest in a complex, always on, high availability architecture to avoid the single point of failure for critical projects.
Security Concerns
The MCP gateway may actually introduce new security concerns (in addition to performing as a security solution).
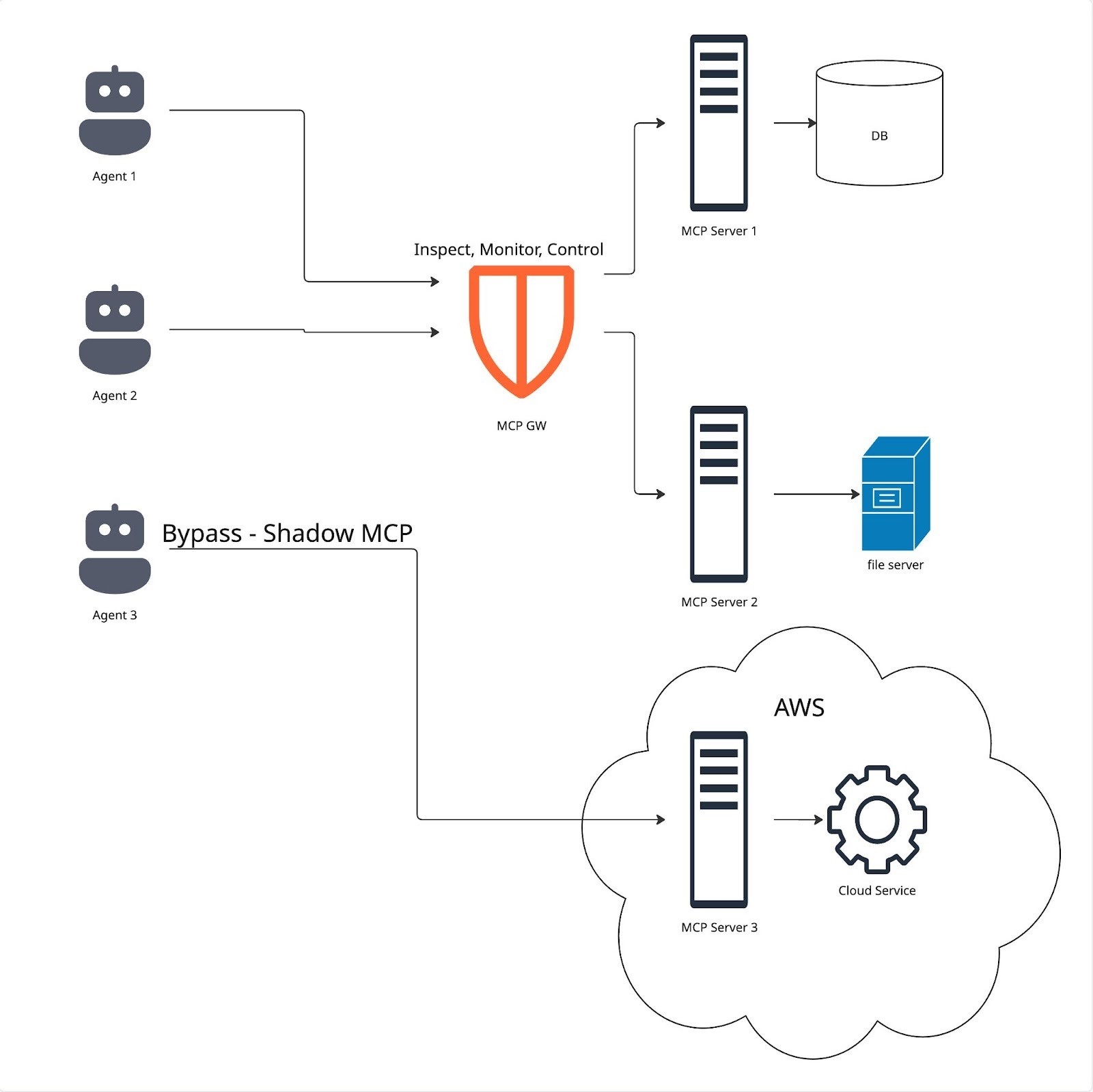
Easy to Bypass
The MCP gateway is fairly easy to bypass. The performance and scale challenges may convince an engineer to bypass the gateway. That will result with increased security risks, an organisational blindspot and the potential introduction of shadow MCP servers.
The gateway as a New Attack Surface
The MCP gateway holds the necessary certificates and private keys to be able to decrypt the MCP traffic between the agent and the server. If an attacker can access the gateway, that person will gain access to the traffic in the clear, to the gateway’s certificates and to the stored private keys and can use that to steal from or damage the organization. That makes the MCP getaway a high value target. It is likely that as an external product, it will come with vulnerabilities and bugs that will enable an attacker to gain control.
TLS Protocol Challenges
The MCP gateway acts as a transparent proxy for the TLS protocol (between the agent to the MCP server). That could introduce several challenges that may either break the communication between the agent and server or pose a security concern.
If the agent and server are using advanced TLS capabilities such as certificate pinning, mutual TLS (for zero trust communication), encrypted SNI and ECH, the traffic may break and the agent will not be able to connect to the MCP server. Those capabilities are recommended by the developers community and are likely to be used in production.
The MCP Server might not be compatible with the latest TLS specs and could downgrade the communication, introducing a security risk or a communication failure.
Governance, Privacy and Compliance
Since the MCP gateway decrypts the traffic between the agent and the MCP server and has access to the session’s data in the clear, this introduces additional concerns around governance and compliance.
Compliance Concerns
The MCP gateway might be exposed to private and sensitive data and may even log or display that information. This may pose a legal challenge in certain cases.
In addition, the MCP server’s access to the decrypted data poses compliance and legal concerns.
Depending on jurisdiction, location and the organization’s responsibilities, decrypting traffic, inspecting it and logging it may trigger stronger requirements over GDPR, HIPAA, PCI-DSS, SOX, labor laws and other regulations, standards and security frameworks. That can increase the cost and the complexity of the agentic AI project.
Operational Complexity
The introduction of the MCP gateway isn’t “free” and incurs significant administrative and operational hurdles.
Certificate Management
As a man-in-the-middle proxy, the MCP gateway must present a trusted certificate to the agent and other GenAI and monitoring tools. This mandates that the organization will add the MCP gateway’s root CA to the list of trusted CA’s and that the MCP gateway will manage private keys and certificates. This adds additional burden to Operations and requires extra management considerations. It is also a security risk that can be exploited by attackers.
Vulnerability Management
The MCP gateway, as a 3rd party component, must be constantly monitored for vulnerabilities, patches and updates. As a critical part of the Agentic workflow infrastructure, it must be on the critical path for security patches and upgrades, adding more burden to the operational process and introducing risk if the patch is late or ignored.
Single Point of Failure
As mentioned before, the MCP server is a critical component that could stop the agentic AI from performing if it fails or breaks. Operations must monitor it constantly and make sure that it is up and active. They should also make sure that it has sufficient CPU, memory and disk resources and that it does not introduce latency and lag to the workflow. In the case where high availability. load -balancing and clustering are introduced, the monitoring and maintenance requirement grow and could be harder to achieve and manage.
Conclusion
In this short blog I tried to point out the numerous challenges that an MCP gateway might introduce to an agentic AI workflow. The MCP gateway might look like a reasonable approach to the security, visibility and control requirements of the agentic AI project but it could also become the reason for the project’s downfall.
For an Enterprise grade deployment, the introduction of the MCP gateway into the agentic AI architecture could cause performance, scale, security, compliance and operational issues that could tank the entire project. Those concerns should be addressed early to guarantee the project’s success.
