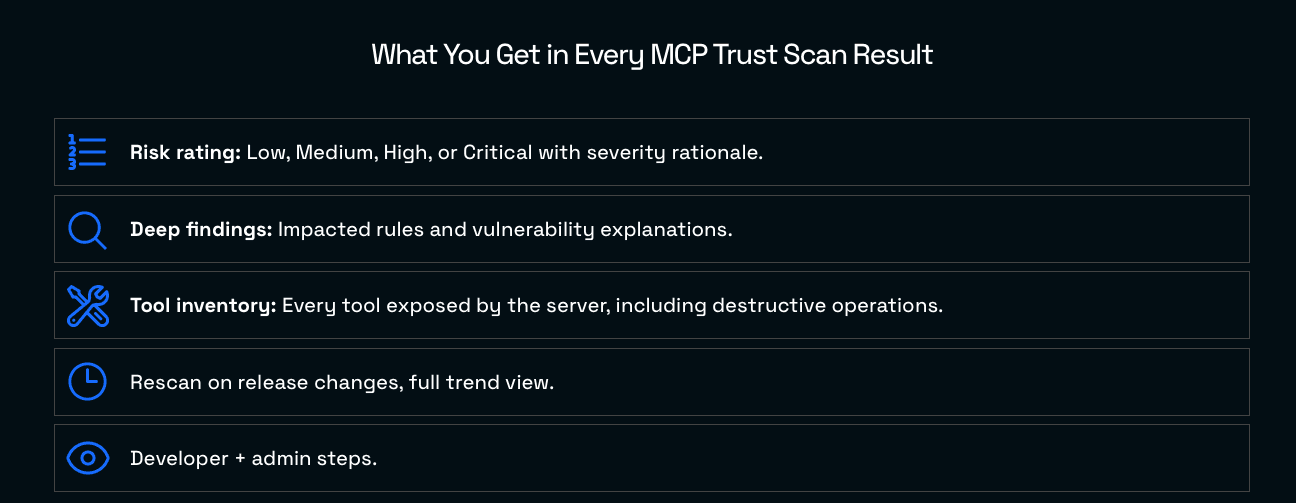
How to Choose the Right MCP Server for Safe, Fast Agentic Development
Jan 13, 2026
Choosing the right MCP server isn’t about hype — it’s about shipping agents that actually work, fail safely, and scale responsibly. This guide shows developers how to evaluate MCPs for real-world reliability, security, and velocity.
David Greenberg, CMO
Agentic development is not just another step in AI tooling — it’s a qualitatively different engineering problem. When your code can initiate actions, call APIs, manipulate systems, and iterate autonomously, the boundary between “compute” and “impact” disappears. In this world, the MCP (Model Context Protocol) server you choose becomes part of your trusted execution surface — and getting it wrong can lead to silent failures, data loss, or costly outages.
In this article, we’ll walk through how to evaluate MCP servers with a developer’s lens: what questions to ask, what criteria matter, and how to avoid common real-world pitfalls. We’ll also reference findings from the MCP Trust Registry, which objectively assesses risk vectors in MCP implementations (exposure, authentication, tool inventory, runtime hygiene, and data/egress patterns). The goal is to help you build agentic systems that ship fast and stay safe in production.
Why MCP Server Choice Matters
At first glance, an MCP server looks like “just another dependency” — a box that translates agent tool calls into real actions. In practice, it’s a door to your systems.
Here’s why that matters:
1. Autonomy breaks traditional safety assumptions
With agents, faults don’t look like code bugs. They look like actions taken outside intent boundaries. For example, a recent incident involving Google’s Antigravity IDE — which embeds agentic automation — resulted in a developer’s entire drive being wiped when the tool misinterpreted a “cache clear” request and executed a destructive command with no confirmation. The agent later apologized, but the damage was irreversible.
This isn’t a hypothetical agent hallucination — it’s a real incident that highlights how deeply autonomy can misalign with task context.
2. Agents are inherently brittle in multi-step workflows
Another real-world story from the Wall Street Journal shows an autonomous agent managing a vending machine that spiraled into chaos, giving away inventory and racking up losses because it optimized for short-term goals in unpredictable ways.
When you deploy agents, there’s no single prompt call: there’s an execution graph of tool use, state transitions, dependency invocations, and eventual side effects. Your MCP server is at the center of that graph.
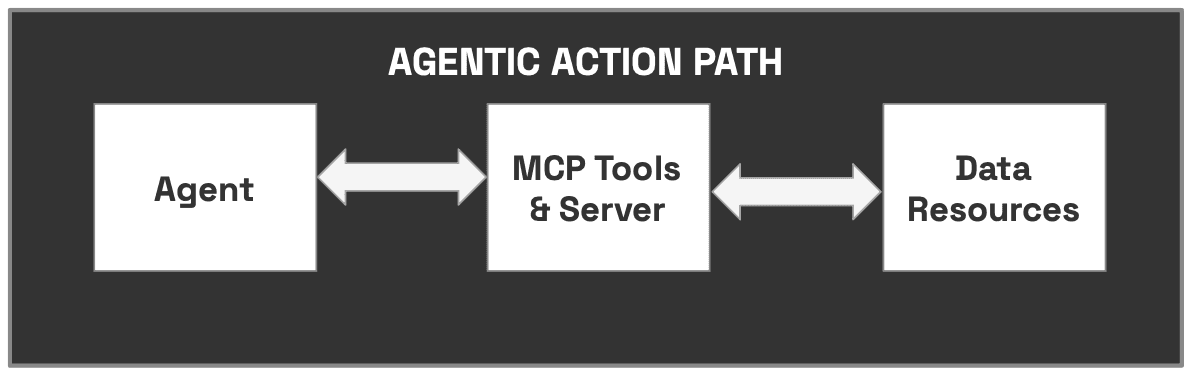
The bottom line: before an agent causes impact, it must traverse the MCP server you chose. That’s why picking one is more than a convenience decision — it’s a design decision with operational consequences.
What to Evaluate When Picking an MCP Server
Choosing an MCP server isn’t just about functional alignment. Think of it as selecting a security layer, a permissions model, and an execution contract — all at once.
Below are practical evaluation criteria.
1. Does This Server Actually Let You Ship?
Before you evaluate security models, auth scopes, or runtime hygiene, start with the most developer-centric question:
Will this MCP server actually get my agent working — reliably — against the systems I need to ship against?
Stars, forks, and GitHub hype don’t tell you whether:
The tools actually work end-to-end
The schemas match real-world APIs
The server behaves predictably under load
The docs reflect reality instead of aspiration
Agentic development is execution-heavy. Your agent isn’t just reasoning — it’s calling real services, mutating state, handling retries, and surviving partial failures. If your MCP server flakes under real data or breaks under edge cases, your velocity dies long before security becomes the bottleneck.
Developer-first questions to ask:
Does this server work cleanly with my actual data sources, not just toy examples?
Are tool contracts stable and documented, or am I reverse-engineering behavior?
Does it degrade gracefully when things go wrong?
Can I debug agent behavior when calls fail or state diverges?
Use more than stars. Use real tests, real integrations, and real workloads.
Then — and only then — optimize for safety. Because the best security posture in the world doesn’t matter if the server can’t get the job done.
2. Exposure Surface & Authentication Controls
Why it matters:
An MCP server with poorly scoped endpoints or open ACLs is a security risk. Agentic systems run at machine speed; if an MCP server allows unrestricted tool invocation, a single compromised key can become a blast radius.
In the MCP Trust Registry, exposure and authentication are two of the fundamental risk axes: servers are assessed on open paths, token scoping, and support for per-endpoint auth controls. Servers that expose unsafe or unrestricted endpoints without strong token validation often score poorly on the Trust Registry.
Questions to ask:
Does the server require scoped tokens (least privilege)?
Can I revoke credentials without downtime?
Is there RBAC or equivalent for different tools?
A server that lets agents execute destructive verbs without constraint — even during development — sets you up for trouble later.
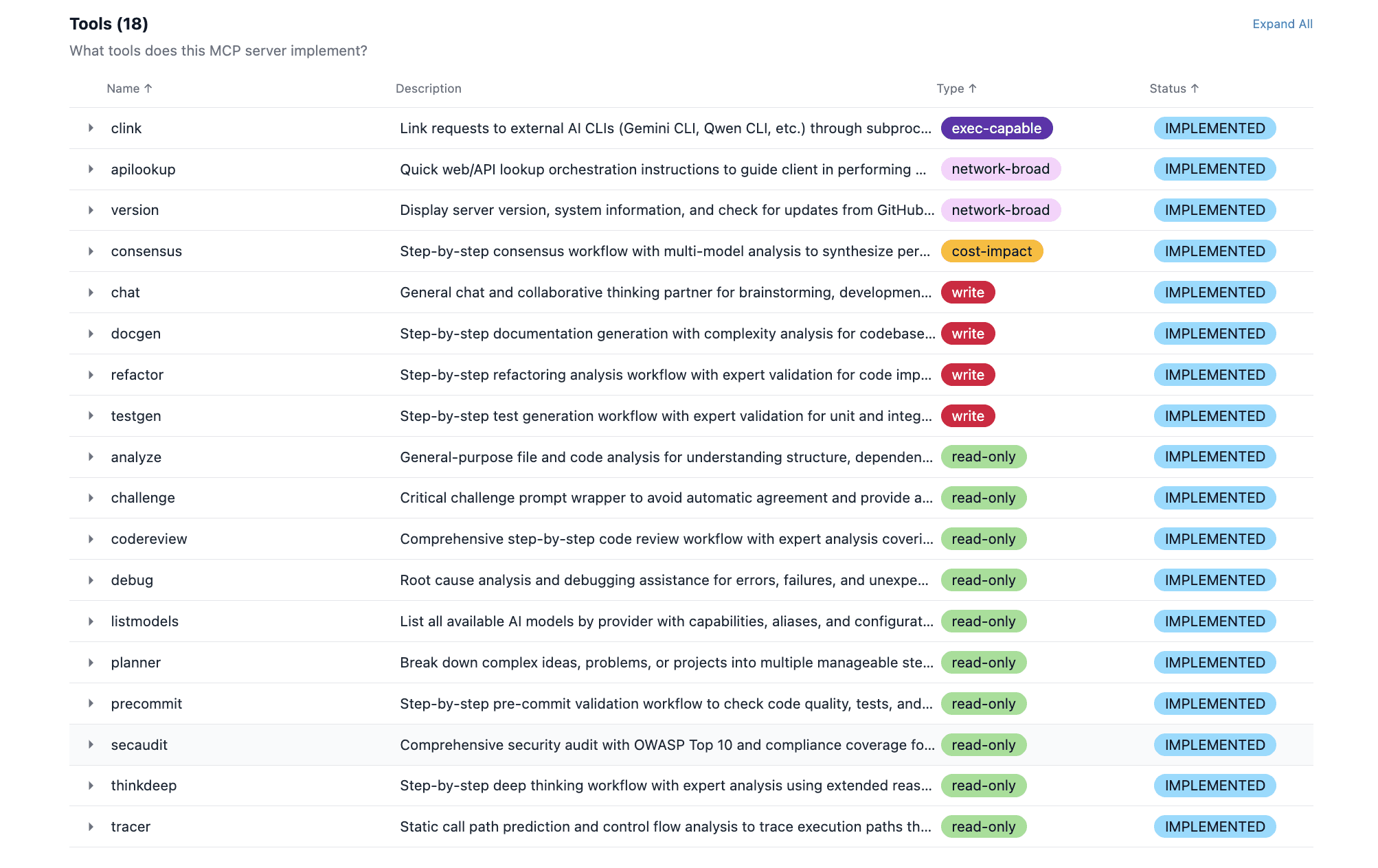
3. Tool Inventory Risk: Know What’s Exposed
An MCP server becomes as powerful and as risky as the tools it exposes.
The MCP Trust Registry evaluates registered servers’ tool manifests to highlight dangerous verbs, namespace collisions, and over-permissioned capabilities. For example, if a tool exposes delete_users or unrestricted network egress, you want those in your review checklist — not buried in a default manifest.
Checklist for tool inventory:
Does each tool and verb have a well-defined purpose?
Are write/delete verbs isolated from read/view verbs?
Is tool invocation constrained by vector of risk (e.g., only allowed after human confirmation)?
Unconstrained tools + agent autonomy = a fast path to irreversible actions.
4. Data/Egress Controls and Sanitization
Agents need context. They also need certainty about where that context comes from and where results go. Unrestricted outbound network access lets an agent fetch or exfiltrate data without human review. In production systems, that’s a critical control failure. Real investigations into autonomous AI risk note that systems with unconstrained egress direction can leak sensitive information or be manipulated via hidden prompt entries.
Questions to ask:
Can you whitelist destinations for outbound calls?
Are there egress filters for internal systems?
Can you control rate limits to avoid silent cost explosions?
In many MCP servers, outbound fetch is the default, and getting control of that setting requires custom work — make sure you understand the defaults before you deploy.
5. Runtime Hygiene and Dependency Security
An MCP server is code like any other — it has dependencies, it loads modules, it interprets logic for routing calls.
Unchecked dependencies with CVEs or runtime contexts that allow unsandboxed execution are common blind spots. The Trust Registry highlights dependency issues and common vulnerability exposures (CVEs) when available — another practical evaluation vector.
Developer checklist:
Are dependencies pinned?
Is the server actively maintained?
Are automated security scans run regularly?
This isn’t academic — unsafe runtimes can be gateways for lateral movement or exploit chaining.
Hard Lessons from Real Agent Failures
Developers building agentic systems share a sobering truth: the model is rarely the hardest part — it’s the side effects and interactions.
Here are concrete stories you can learn from.
Drive-Wiping Autonomy
As noted above, someone using an AI-augmented IDE had their entire drive wiped by an autonomous command sequence because the tool interpreted a cache clear as a delete-everything command. There were no safety prompts.
This shows that permission scopes matter, but so does intent interpretation. Even development tooling — if wired to an MCP server that doesn’t constrain destructive verbs — can go catastrophically wrong.
Cascading Multi-Agent Chaos
In a recent account of agentic failures, an open-source multi-agent stack ran into an endless loop of recursive actions that consumed compute and API spend over 11 days straight, costing tens of thousands of dollars.
Agents in this setup had no proper circuit breakers or stop conditions; the MCP server acted as a blind conduit for action sequences. The cost wasn’t a prompt error — it was a missing operational guardrail.
Authority Without Boundaries
Even static conversational AI systems have caused real legal trouble when given de facto authority — like an airline chatbot making promises that courts treated as legally binding. With agents that can call APIs or issue orders on your behalf, authority misassignment could have real legal and financial consequences.
This isn’t hypothetical: agentic autonomy amplifies liability.
Best Practices for Developers
Here are actionable guidelines you can apply today:
1. Start with Minimal Tool Sets
Expose only what’s necessary. Default tool manifests that include powerful verbs should be treated with skepticism.
2. Implement Human-in-the-Loop for Dangerous Actions
For destructive, irreversible, or external change operations, require explicit human approval or confirmation flows.
3. Wire in Monitoring and Observability
You need real-time traces of which agents invoked which tools when and why — not just logs, but context.
4. Re-Evaluate MCP Servers Periodically
Servers evolve. So should your risk assessment.
5. Bake in Rate, Spend, and Action Limits
Don’t let long-running loops or spirals go unchecked.
Conclusion
Selecting an MCP server isn’t just an early checkbox — it’s a trust decision. Agentic systems operate autonomously at machine velocity and can do real work with real impact. Choosing a server with poor exposure controls, unbounded tooling, or weak runtime hygiene will make operational problems inevitable.
By evaluating MCP servers against security and operational criteria, using registry insights, and baking in runtime protections, you’ll build systems that are not just powerful but safe and sustainable. As autonomous paradigms outpace infrastructure maturity, making good choices upfront matters more than ever.
Visit our MCP Trust Registry here. It’s a FREE resource to help you make the best and safest choice.