BlueRock Runtime Reachability & Real-Time App Guardrails:
Attackers now move at AI speed.
Scan/patch can’t keep up — and detect/respond security agents react too late.
The Answer: It’s time for a Compute Firewall.
Legacy Scan & Patch
Can't Fill The Gap
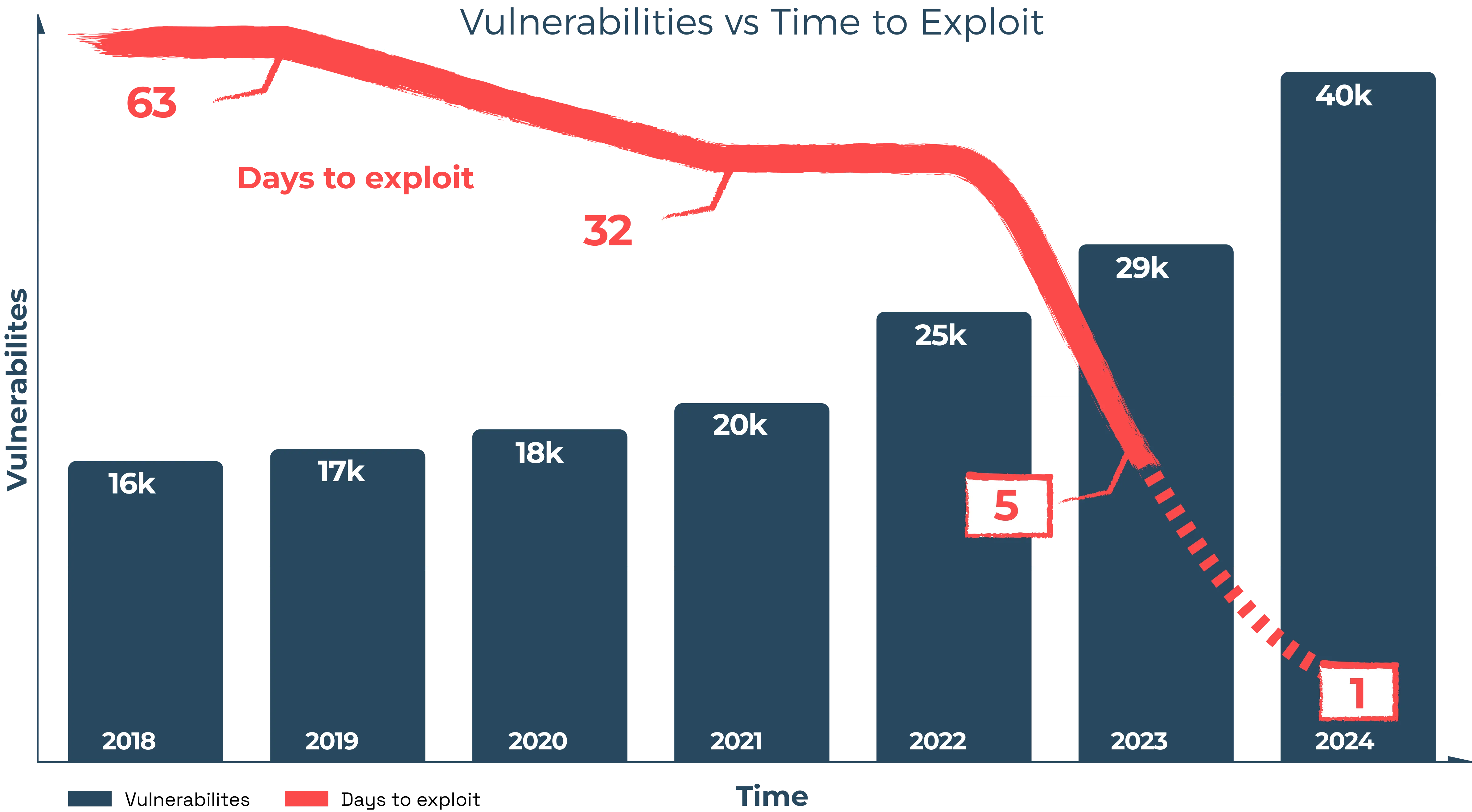
In the era of AI-speed attacks, SCA, SAST, and DAST tools can’t keep pace. Remediation windows are shrinking all while vulnerabilities from 3rd party libraries and AI-generated code are exploding.

Too Irrelevant
unused libraries treated just like internet-facing code.

Too Overwhelming
developers can’t innovate and patch thousands of CVEs.

Too Misaligned
irrelevant CVE patch lists create friction between dev and security teams.
The real question left un-answered: “Which vulnerabilities matter right now?”
Security Agents
Can’t Fill The Gap
Runtime security tools rely on agents, telemetry and complex analysis to detect, then respond, to attacks. This makes agents a poor foundation for real-time enforcement:

Too Noisy
Legacy Detection & Response solutions can't keep up, are too late, too noisy, & waste security teams' time.

Too Complicated
tuning policies requires deep expertise and constant care.

Too Slow
Negative performance impact of agents on apps is often high and unpredicatable.
The result? Most organizations are still watching—and hoping someone spots an attack and responds in time.
Runtime Reachability & Enforcement Belong in Compute
It’s time to look beyond static code scanning and legacy bolt-on security agents.
- Reduce CVE patch requirements by up-to 90%.
- Stop AI-speed attacks while slashing noise and false positives.
- Zero Friction: No dev slowdown. No app breakage.
Here's How It Works
Patch on your time.
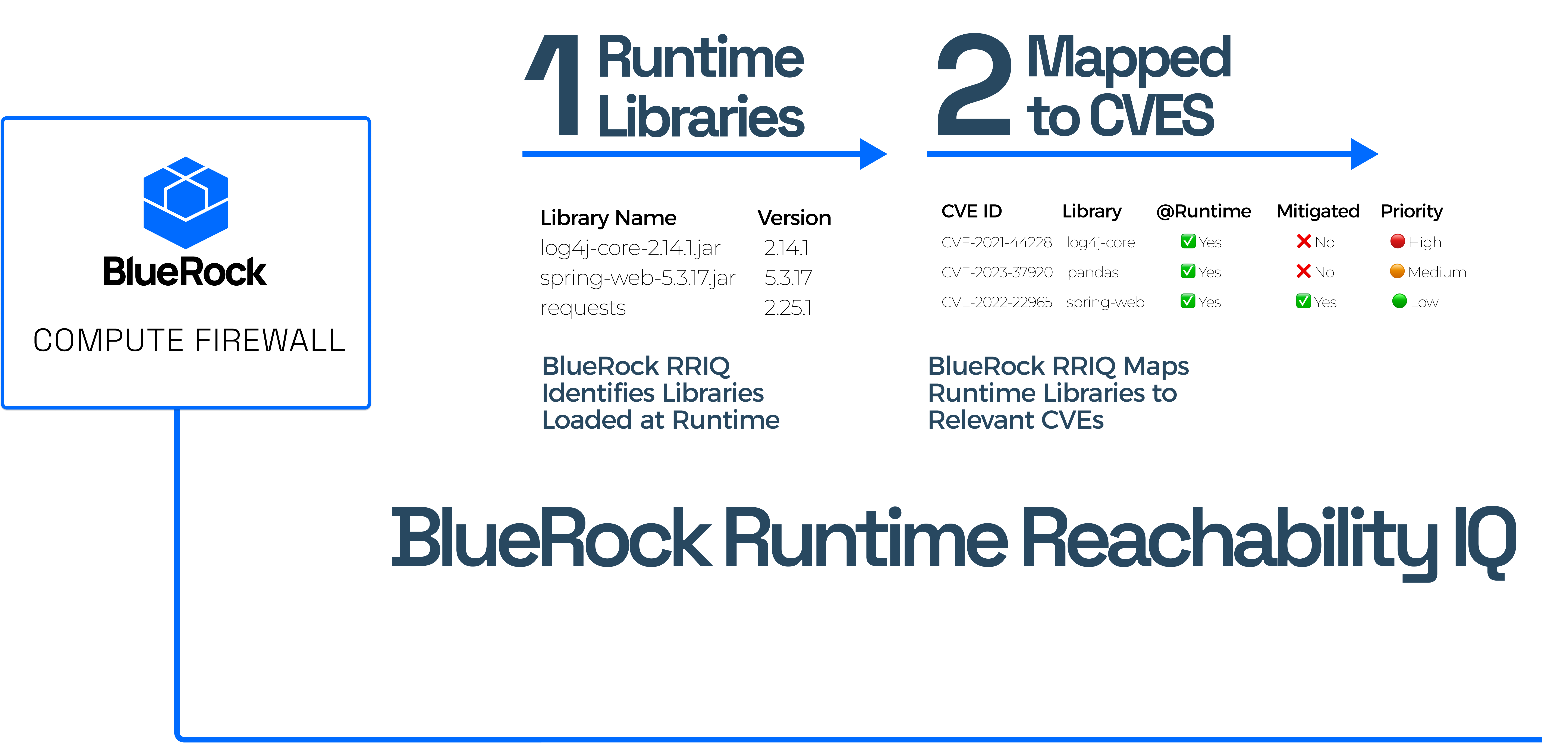
BlueRock Evidence of Vulnerability Coverage (EVC) leverages a multi-model AI inference system to analyze CVE characteristics, mapping exploit exposure to known attack paths and those BlueRock mechanisms which provide a runtime compensating control. This gives you the ability to prioritize which vulnerabilities are most critical to patch .
Respond Less.
BlueRock Runtime eXecution Guardrails (RXG) delivers proactive, real-time attack prevention across applications, containers, and host/OS runtime environments. Integrated transparently in cloud-ready images, it's always-on — removing the need for yet another security agent — and protects workloads without requiring developer code changes.
Actionable Vulnerability Intelligence
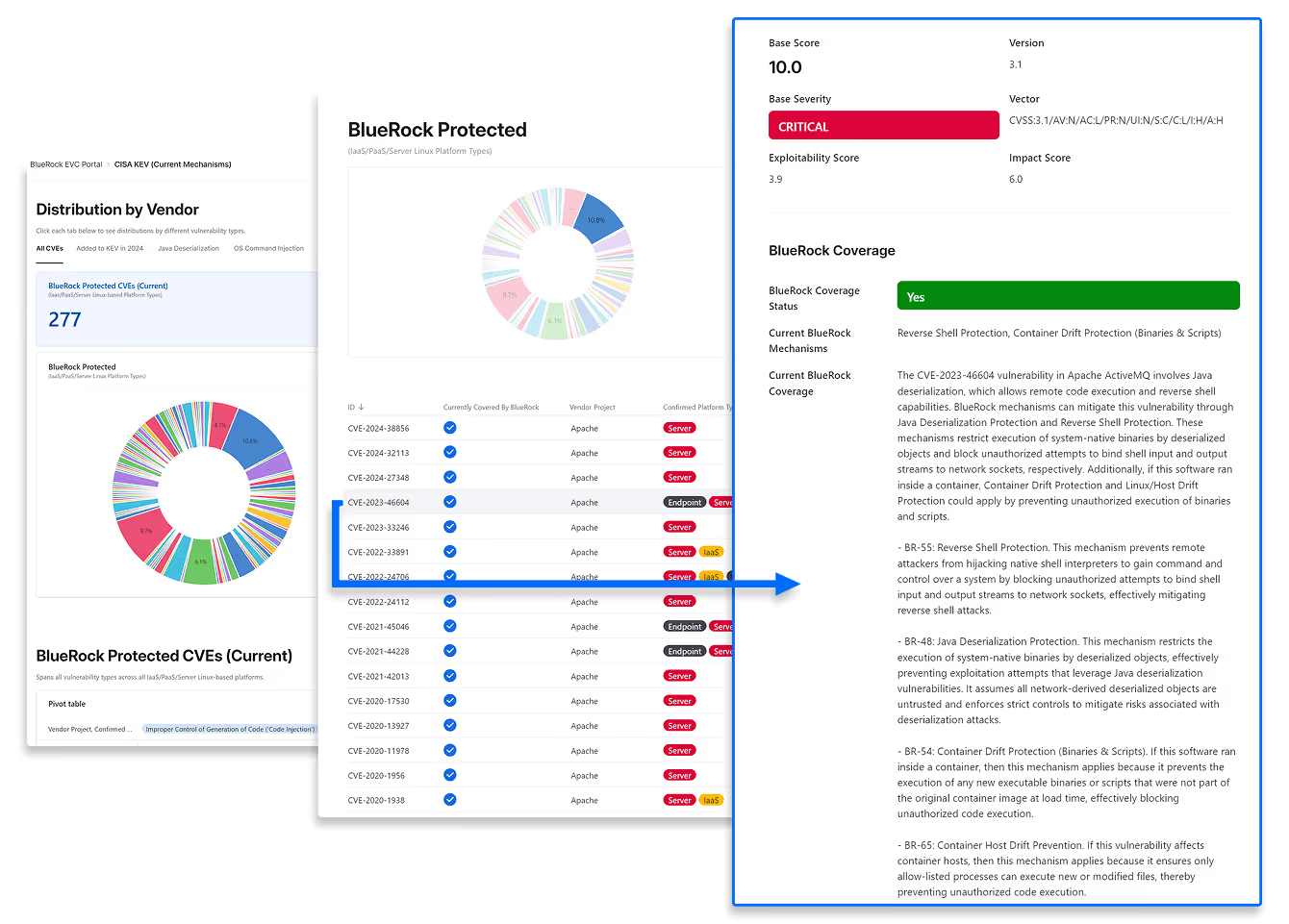
Simplify Vulnerability Management
BlueRock reduces the set of CVEs security teams need to juggle and helps prioritize the ones that matter. Have 5+ year old CVEs? BlueRock’s automated deep research can analyze any CVE on-demand.
Easy Evidence of Compliance
Trying to achieve or maintain SOC2, PCI, HIPAA, or ISO 27001 compliance? BlueRock provides up-to-date explainable evidence of coverage to your auditors to help with rapid certification and re-certification efforts.
Rapid Response: AI-driven vulnerability insights—even when new zero-day threats emerge.
Transparent Analysis: Detailed breakdowns of how each CVE is neutralized.
Comprehensive Coverage: Not just the headline threat—EVC analyzes the full chain of vulnerabilities.
Optimized for Your Workloads: Specifically tailored for Linux servers and container environments.

“Shift Down” Security
BlueRock Runtime eXecution Guardrails (RXG) neutralizes threats at runtime—before they can execute—instead of reacting after an attack happens.
Real Runtime Security Stops Attacks Cold
Unlike traditional "Detection and Response", methods that rely on noisy telemetry and react after attacks have already occurred, BlueRock runtime security proactively halts attacks in real-time.
Multi-Layer Attack-Chain Defense
BlueRock attack prevention spans Application, Container and Host/OS runtime environments, providing advanced runtime guardrails that block attacks while maintaining high workload performance and eliminating false positives.
Not Another Security Agent
BlueRock’s solution isn't yet another security agent; it's a cloud-ready machine image featuring built-in, transparent security controls that safeguard workloads without requiring developers to modify their applications.
Try For Free.
Available in AWS Now!
Three Key Insights

Insight #1 – Don’t Just Shift Left
Shift-left practices have value, but in today’s world of AI-speed attacks, they aren’t enough. Developers are already drowning in patch pipelines and scan alerts for known CVEs. Worse, attackers are now able to discover and exploit new vulnerabilities at AI-speed and scale.
Insight #2 – Focus on the Middle of the Attack Chain
Modern attacks don’t get blocked at network ingress. Attackers now have countless ways to gain an initial foothold. And yet to achieve their objective they must chain together a smaller and predictable set of actions which can be seen and stopped with high precision.
Insight #3 – Shift Down to Secure the Compute Runtime.
“Shift Down” Security means moving enforcement into the runtime layer – not as “yet another security agent” but integrated into the machine image distributions you already use, giving you always-on runtime protection that is transparent to developers, ensures fast app performance, and stops attacks in real-time.
Compute Firewall

The Firewall Isn't Dead.
It's In The Wrong Place.
Unlike Shift-Left Scan/Patch methods which are unable to address the risk of unpatched and unknown vulnerabilities, BlueRock protects workloads at runtime with CVE-agnostic guardrails capable of thwarting entire classes of attack chains.
Unlike noisy agent-based approaches that detect first, then respond, BlueRock protections enforce precise invariants across apps, containers and hosts, avoiding false positives and stopping entire classes of attack chains originating from exploits of known and unknown vulnerabilities, alike.