BlueRock Runtime
Reachability IQ
Save time. Fix what runs.
Where Your Compute Firewall Journey Begins
BlueRock Runtime Reachability marks the first milestone in your Compute Firewall Journey, revealing which vulnerabilities truly matter by focusing on what actually runs.
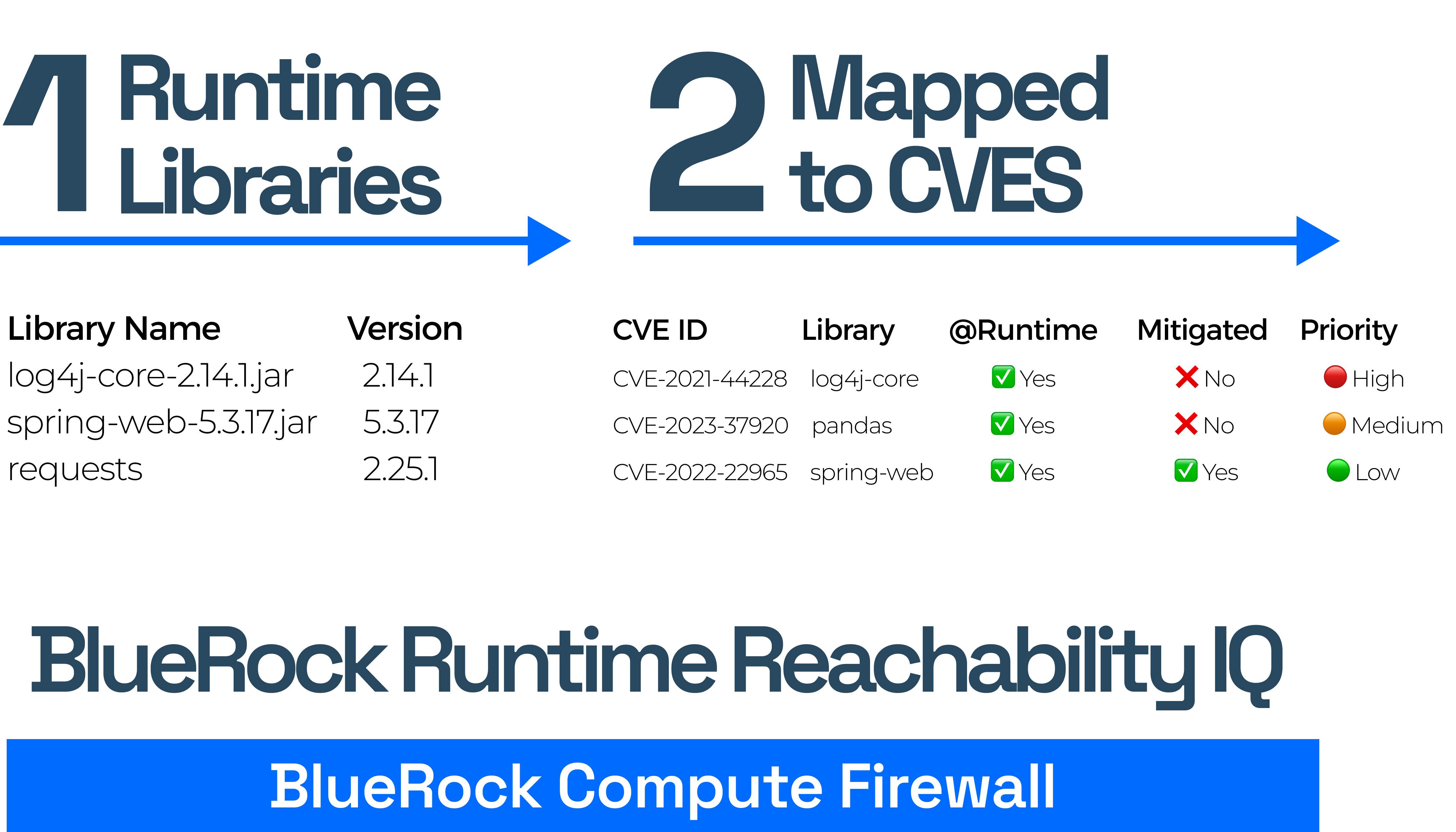
Step 1:
Runtime Reachability
Flip the script on static SCA code scans. Start with what’s running. Prioritize what’s reachable.
Step 2:
Runtime Obseravibilty
Full-context attack chain visibility spanning application, container and node runtimes.
Step 3:
Runtime Enforcement
CVE-agnostic policies block attacks in real-time. 5 simple rules stop 70% of known exploited vulnerabilities.
BlueRock Compute Firewall
Ubuntu | Amazon Linux | Bottlerocket
The sheer amount of code in apps and 3rd party libraries is amassing exponentially, driven by the rise of AI-assisted development and “vibe-coding”.
At the same time, AI has drastically reduced the time it takes for adversaries to find and exploit vulnerabilities, from months to minutes.
Attackers Have the Upper Hand
From Vulnerability Overload to Runtime Protection
BlueRock Runtime Reachability Intelligence (RRIQ) flips the script on the scan-and-patch cycle.
Traditional scanners (SCA, SAST, DAST) overwhelm developers with CVEs linked to code that never runs. BlueRock RRIQ zeroes in on the libraries and functions that actually execute in production, mapping them to the most important vulnerabilities to patch.
The result: Less noise. No fire-drills. Real runtime protection.

It's About Time
With runtime reachability from BlueRock RRIQ, combined with exploit-chain analysis and runtime execution guardrails from BlueRock EVC and BlueRock RXG, teams cut CVE triage by up to 90% and align security and development on the risks that matter most.
Business Impact: Saves 1 day per sprint per developer to focus on driving innovation, instead of patching useless vulnerabilities.