BlueRock Runtime
Observability &
Enforcement
Agent-less runtime Security protects Apps from known and unknown threats.
Advancing Your Compute Firewall Journey
BlueRock Runtime Observability and Enforcement mark the next milestone in your Compute Firewall Journey, delivered through integrated capabilities of the BlueRock Compute Firewall.
Step 1:
Runtime Reachability
Flip the script on static SCA code scans. Start with what’s running. Prioritize what’s reachable.
Step 2:
Runtime Obseravibilty
Full-context attack chain visibility spanning application, container and node runtimes.
Step 3:
Runtime Enforcement
CVE-agnostic policies block attacks in real-time. 5 simple rules stop 70% of known exploited vulnerabilities.
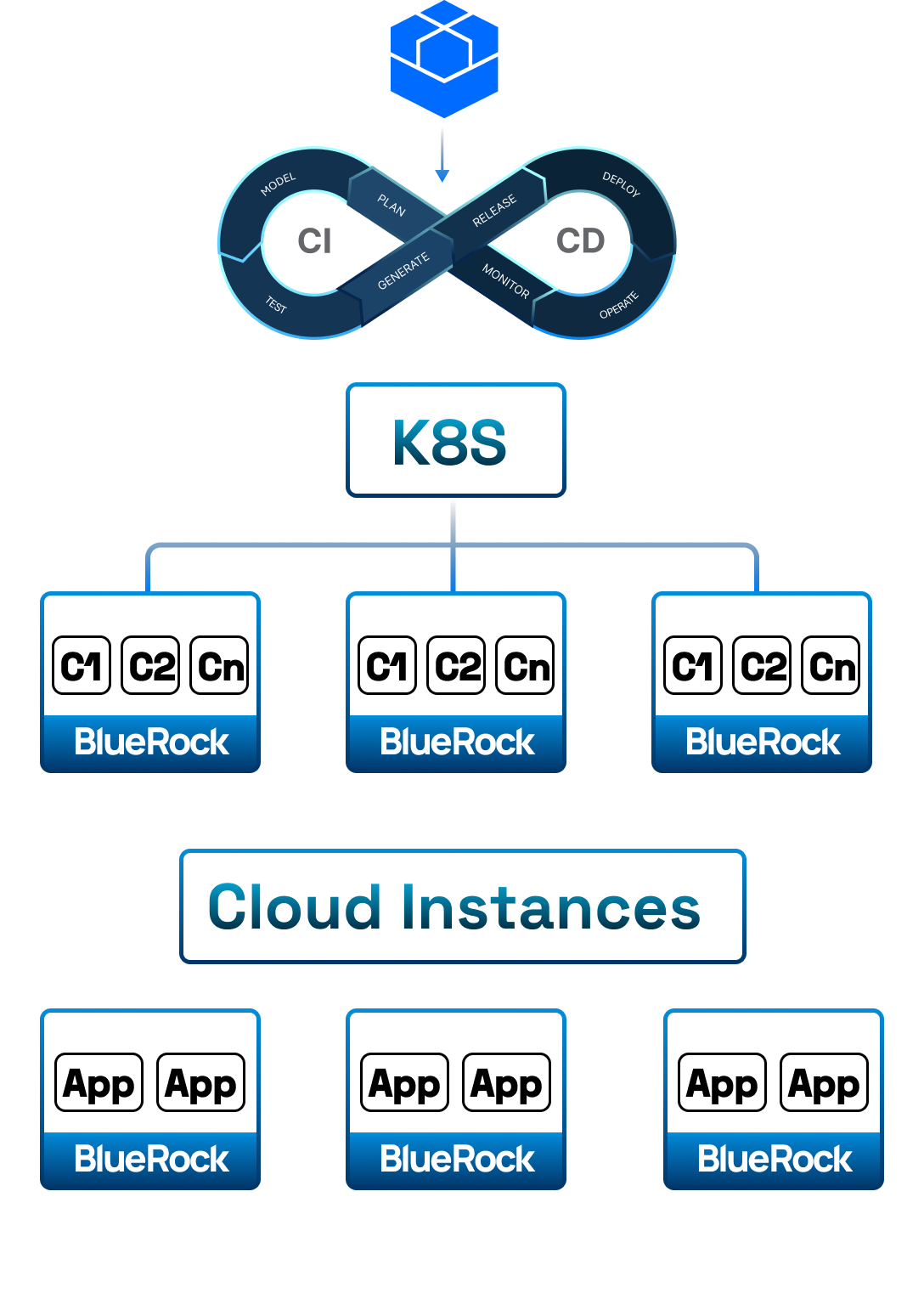
BlueRock Compute Firewall
Ubuntu | Amazon Linux | Bottlerocket
See and Stop Known and Unknown Attacks
BlueRock Runtime Execution Guardrails (RXG) and BlueRock Evidence of Vulnerability Coverage (EVC) components work together to protect what matters most. RXG safeguards apps and runtime platforms with agent-less defenses, while EVC guides developers to the compensating controls that are most critical for security and compliance.
BlueRock RXG
Precise invariant-based runtime guardrails are baked-in to the BlueRock Compute Firewall, providing full-stack runtime visibility and protection for apps, containers and nodes. RXG sees and stops known and unknown exploit chains, without the need for "bolt on" legacy security agents.
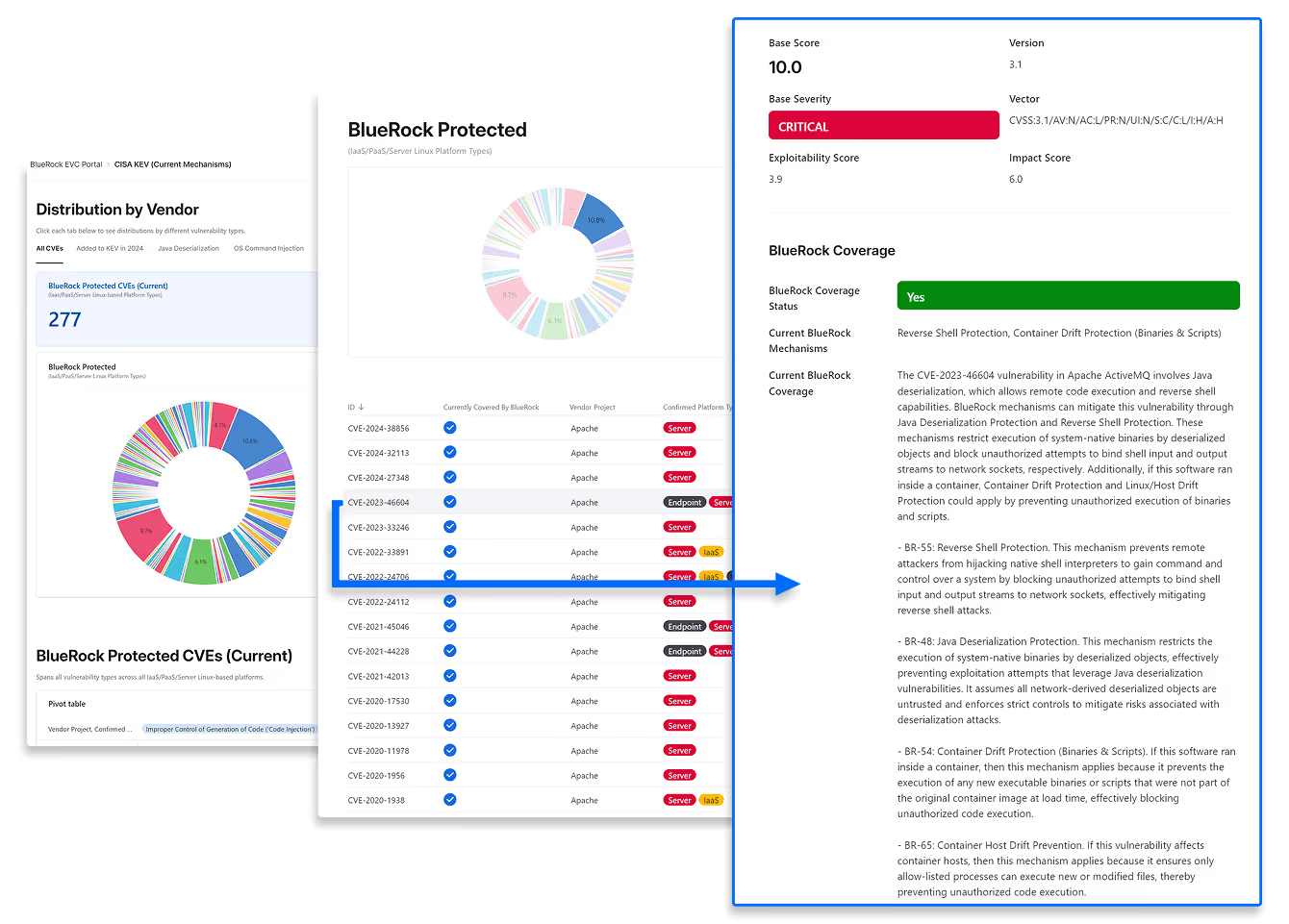
BlueRock EVC
Multi-model AI analyzes CVEs, mapping vuln characteristics to BlueRock RXG guardrails that provide a compensating control. EVC helps developers prioritize the most critical patches and auto-documents coverage for SOC2, PCI, HIPAA, ISO 27001 audits to accelerate compliance.
built to block.
BlueRock RXG
AI is shrinking the time to exploit known vulnerabilities from months to minutes, while enabling attackers to uncover entirely new ones at breakneck speed. BlueRock RXG provides CVE-agnostic guardrails that see and stop entire classes of attacks in real time across apps, containers, and nodes.
Application Guardrails
- Deserialized Object Escapes
- OS Command Injection
- Path Traversal
- Reverse Shell
Container Guardrails
- Container Drift Exec
- Container Capability Hijack
- Namespace Execution
- Container Socket Access
Node
Guardrails
- Process Execution
- Sensitive File Access
- Syscall Overwrites
- OS Credential Overwrites
BlueRock EVC
The sheer volume of app code has surged through AI-assisted development and the use of third-party libraries, making traditional code scan/patch and runtime attack detection untenable. BlueRock EVC redefines CVE patching and runtime protection. Working in concert with BlueRock Runtime Reachability Intelligence (RRIQ) and Runtime Execution Guardrails (RXG), BlueRock EVC helps development teams identify compensating controls that buy developers more time to patch reachable vulnerabilities.
Rapid Response
AI-driven assessments for both zero-day and N-day threats close the gap between discovery and actionable insight.
In-Depth Analysis
Comprehensive exploit-chain analysis, covering known and inferred attacks, guides the selection of effective protection mechanisms.
Clear Insight
Detailed explanations of how compensating controls mitigate unpatched CVEs assures remediation and accelerates compliance.
Transparent Deployment. Full-stack Protection.
BlueRock lives inside the OS images you already use (Amazon Linux, Ubuntu and soon Bottlerocket), enabling DevOps teams to deploy runtime security with already existing CI/CD workflows. No app code changes. No "bolt on" security agents. Just frictionless runtime security.
Built-in protection. Just 5 simple policies stop 70% of CISA Known Exploited Vulnerabilities (KEVs).
Agent-less runtime protection that covers apps, containers, and nodes.
Native support for OTEL-enabled observability tools and automated deployment frameworks such as Terraform and AWS Cloud Formation.